




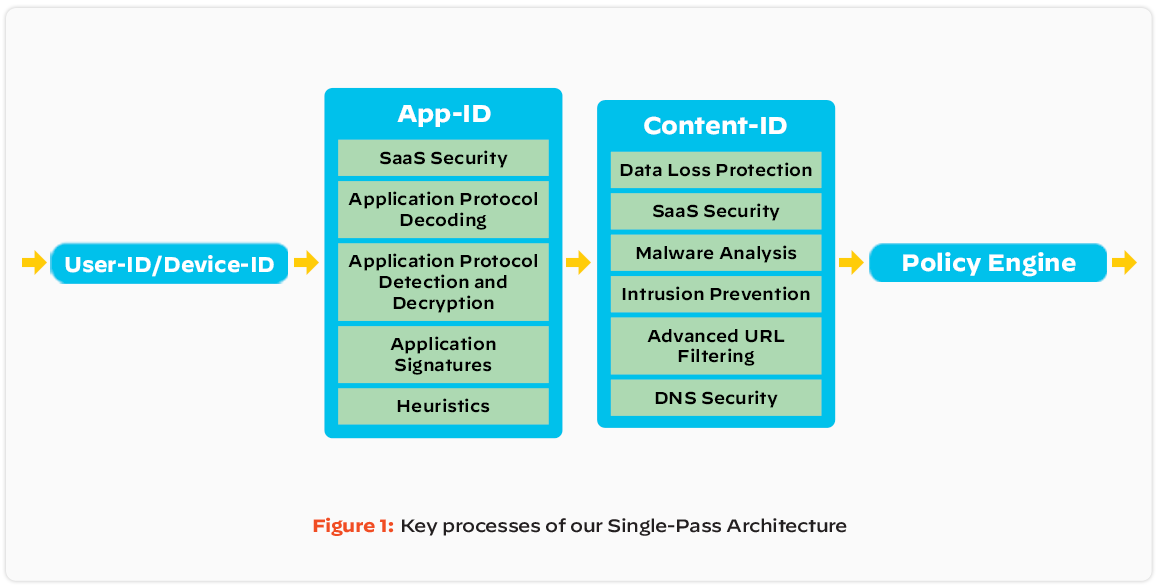

Palo Alto Networks firewalls classify network traffic by application identity to grant users access and provide administrators with visibility and control of all types of applications, including web applications, software as a service (SaaS) applications, and Legacy applications. Our approach uses applications rather than ports as the basis for all your security enablement policy decisions, so you can allow, deny, schedule, inspect, and apply traffic shaping. When needed, you can create custom App-ID™ tags for specific applications or request the development of an App-ID for new applications.
√ Block malicious files and thwart data exfiltration attempts.
√ All applications on all ports are always identified and classified.
√ Enable secure migration of legacy Layer 4 rule sets.

ML-based NGFW uses embedded ML algorithms to realize wire-speed classification, inspect files as they are downloaded and block malicious files before they could cause damage. With online prevention, PA Series automatically prevents initial infections from never-seen threats without the need of cloud-based or offline analysis of most malware variant threats, thus shortened time between visibility and prevention to nearly zero. Inline ML- supported prevention helps protection against the most challenging and prevalent threats, including portable and executable files, phishing, malicious JavaScript, and fileless attacks. Finely tuned models avoid false-alarm, and a unique feedback loop ensures continuous accuracy.
√ Discover malicious files in real time as they enter your network.
√ Maintain safety performance with single online inspection.
√ Reduce the time to identify and block unknown threats to almost zero.

Palo Alto Networks Cloud Identity Engine is a cloud-based identity-based security architecture that consistently authenticates and authorizes users regardless of where their identities are stored— locally, in the cloud, or a mixture. As a result, security teams can effortlessly allow all users to access applications and data anywhere and quickly move toward a zero-trust security posture.
Cloud Identity Engine saves you the time and trouble of deploying and managing identity-based controls on your network security infrastructure using point-and-click configuration and real-time identity synchronization.
√ Consistently authenticate and authorize regardless of users’ location.
√ Execute security decisions precisely for all users at all times.
√ Save time deploying and managing identity-based controls.






